You are here :
DDoS attacks: how can you guarantee the security and accessibility of your infrastructure?
Published on March 2, 2021 by Laure
-
Updated on 14 mai 2024 à 14H04
With the ever-increasing flow of data on the web, DDoS attacks are on the increase. It is therefore essential to strengthen the security of IT infrastructures in order to guarantee the continued availability and performance of systems in the event of a DDoS attack. What are the different types of DDoS attack, how do they work and how can you protect against them? All the answers in this article!
What is a DDoS attack?
A DDoS attack (distributed denial-of-service attack) is an attack aimed at partially or totally unavailability of a server, service or infrastructure, so that its Users can no longer access it, or their browsing experience is sufficiently degraded that they decide to leave the site.According to Joris Dedieu, Technical Manager at NFrance, " in recent years, DDoS attacks have become much more violent and massive. The development of connected objects and fiber links provides attackers with almost infinite capabilities. With a 1 Gbps fiber using DNS amplification, an attacker can generate an attack of up to 70 Gbps. "
The different types of DDoS attack
There are 4 types of DDoS attack:
- Volumetric attack Volumetric attack: an attempt to exhaust bandwidth to cause congestion, within or between the targeted network/service and the rest of the Internet.
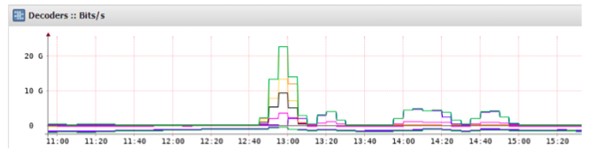
Volume attack at over 20 Gbps
- Lhe TCPdepletion, the aim of which is to asphyxiate the connection status tables of an IT infrastructure (firewalls, load balancers, application servers, etc.).
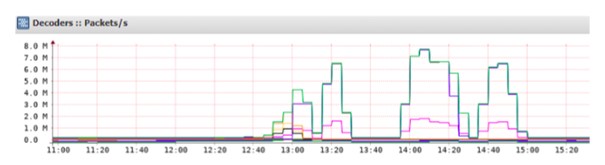
Volume attack at nearly 8 million packets per second (syn flood)
- Attack aimed solely at the application layer
They aim to saturate web servers. " Often small-scale, as they require complete control of the equipment. The best known is Slow Loris, which uses a design flaw in the Apache HTTPD server. "
- Indirect vector attacks
Instead of carrying out an assault on the site, the hacker attacks an important means of its availability, such as DNS, datacenter air conditioning, a network operator. "The best example is the 2016 attack on the Dyn DNS service, which caused outages on Twitter, Ebay, Netflix, GitHub and PayPal."
How does a DDoS attack work?
The cybercriminal begins to saturate the network with requests by overloading bandwidth or exhausting system resources, so that the server can no longer handle all the requests and becomes unavailable.
For example, to carry out a DDoS attack on a distributed network overloaded with requests, cybercriminals use a tool called a botnet, also known as a "zombie network". This network is made up of several Trojan-infected machines or vulnerable connected objects such as routers or IP cameras. To paralyze the distributed network, the cybercriminal launches massive attacks from this infected network, making multiple requests from computers remotely controlled via the malware. Several rebound techniques are available to anonymize and amplify the attack.
Joris Dedieu, Technical Manager at NFrance

How does NFrance combat DDoS attacks?

To guarantee the accessibility of a server, an infrastructure and a service, NFrance offers a defense strategy based mainly on security network security.
Based on a holistic approach, this network security integrates firewalls and other essential security features such as anti-DDoS detection and neutralization tools like Wanguard, network capacity sizing twenty times greater than actual site requirements, a state-of-the-art DNS infrastructure, a direct peering policy with access providers, as well as application transaction control based on HAPro.s, state-of-the-art DNS infrastructure, direct peering with ISPs, and HAProxy-based application transaction control.
Joris Dedieu
These network-wide security solutions are capable of interacting with each other within an integrated, collaborative security environment. In this way, they provide complete protection for a company's entire attackable surface.
NFrance works in particular with the world of education. Institutional sites in this sector are subject to violent attack campaigns, prompting NFrance to multiply its network capabilities. In fact, following an attack, NFrance undertook to increase its network capacity for one of its Local authority customers by a factor of 4, and to invest in a direct connection with the operator Orange. So, even in the event of a massive attack, Bouygues, SFR and Orange customers, as well as all Schools, will continue to have optimum access to Services.Joris Dedieu
